Over 19,000 card details from 22 Pakistani banks stolen in cyber-security breach
How did the security breach take place? Which Pakistani banks and banking consumers have been affected?
November 06, 2018
Recent reports of a massive cyber security breach have shaken up the local banking industry, with the Federal Investigation Agency’s (FIA) cyber-crime chief saying "almost all major Pakistani banks" have been affected.
Cyber security experts say details of more than 19,000 debit cards from 22 Pakistani banks have been stolen in the cyber theft, the biggest of its kind to hit the country's banking system.
But how and when did the security breach take place? How many banks and banking consumers have been affected?
Here is a breakdown of what we know so far based on our conversations with cyber security experts.
What do we know so far?
On the morning of October 27, officials at Bank Islami were puzzled when they noticed abnormal transactions of unusually large amounts on one of its international payment card schemes.
During these transactions a cybercrime group cashed out $2.6 million, according to global cyber security firm Group-IB.
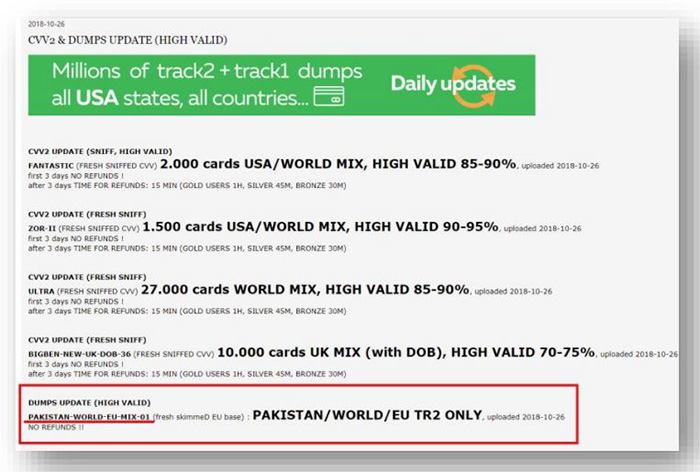
The report IB said hackers had released a new dump of Pakistani credit and debit cards on dark web forums on October 26.
"Analysis of previous incidents suggests that it was linked to the breach," said Group-IB.
The hackers put up the dump, titled "PAKISTANWORLD-EU-MIX-01" with over 10,467 records, on sale on Jokerstash—a virtual Darkweb hub of stolen card data used by hackers as a distribution point for compromised accounts.
More than 8,000 of the cards in the dump belonged to at least nine Pakistani banks and were available for prices ranging from $100 to $135 each.
Bank Islami issued a press release on Oct. 28 announcing that they had become the victim of a cybercrime attack.
The State Bank of Pakistan (SBP) followed by issuing its own security instructions, saying the compromised cards were cashed out via ATM and POS in different countries including USA and Russia.
The central bank's advisory prompted at least six Pakistani banks to temporarily suspend international cash withdrawal transactions though their debit cards.
"It is probable that the cards were compromised before 26.10.2018, and then part of them were used by the cyber-crime group to cash out via the international payments network and other cards were sold to Jokerstash cardshop," Group-IB said.

The name chosen by the hackers —"PAKISTANWORLD-EU-MIX-01"—suggested it was only the first part of a larger dump of data, it said.
But just when everyone thought the storm was over, a second dump appeared on the Darkweb on Oct. 31 comprising approximately 11,000 cards from as many as 21 Pakistani banks.
"The second dump did not include cards from Bank Islami, but cards from several other banks were found," Qazi Mohammad Misbahuddin Ahmed, CEO of cyber security firm PakCERT told Geo News.
He said the new cards were being sold on the Darknet for $100 to $160.
Which banks are affected?
According to PakCERT's Threat Intelligence report, a total of 19,864 debit card details belonging to 22 Pakistani banks are being sold in the dumps circulating on the Darknet.
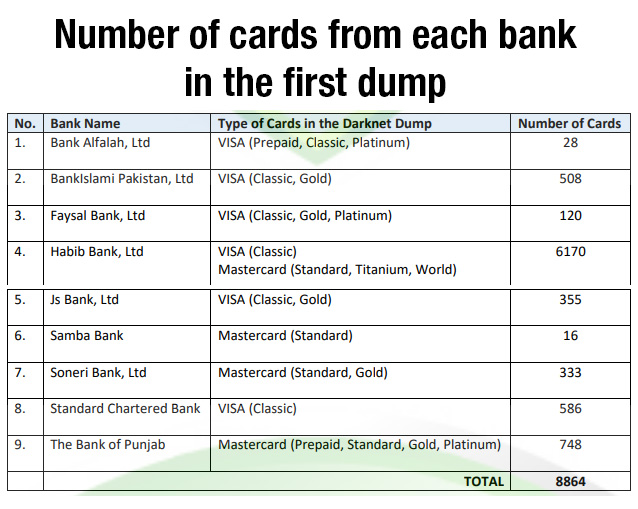
In the first dump released on Oct 26, the majority of cards were of Habib Bank Limited (6,170), followed by the Bank of Punjab (748) and Standard Chartered Bank Limited (586).
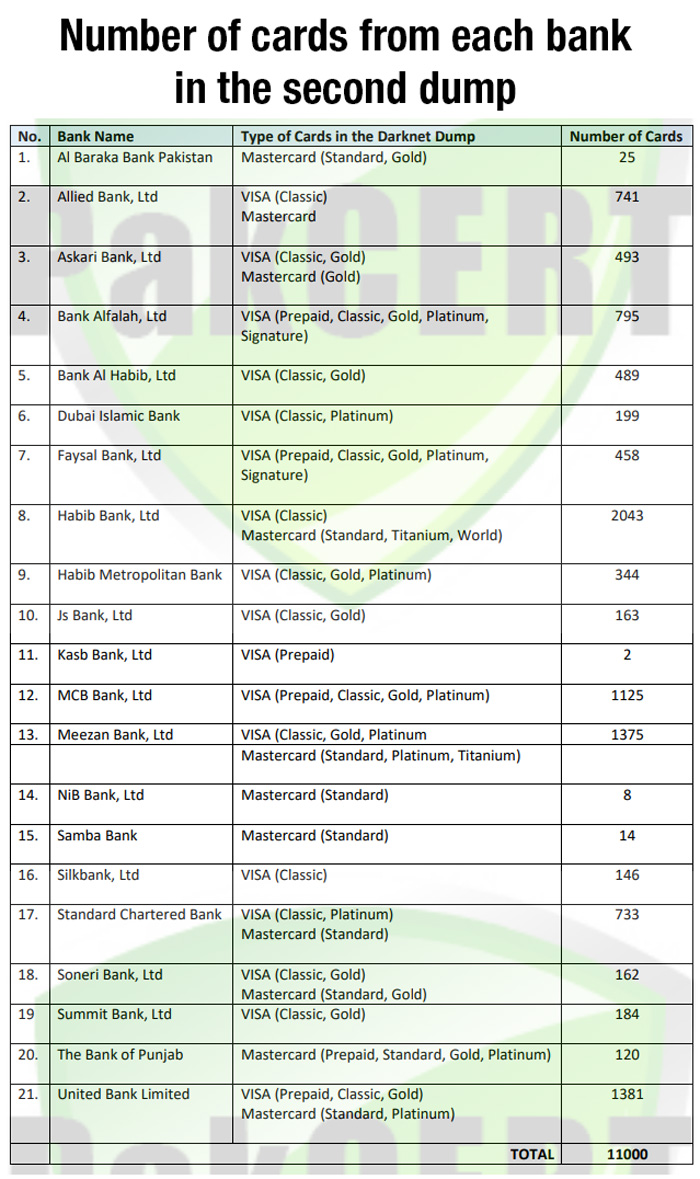
In the second dump released on Oct 31, the majority of cards were of Habib Bank Limited (2,043), followed by United Bank Limited (1,381) and Meezan Bank Limited (1,375).
The dumps included both Visa and Mastercard.
How did the security breach take place?
But how did the security breach actually take place? How were the card details stolen? Did the hackers infiltrate the servers of Pakistani banks?
FIA officials have so far only confirmed the existence of the dump, saying it includes card details from "almost all major Pakistani banks". They have so far not released any information as to how the cyber attack took place.
But details of the transactions, the format of the data, and observations by security experts give a little insight into what might have taken place.
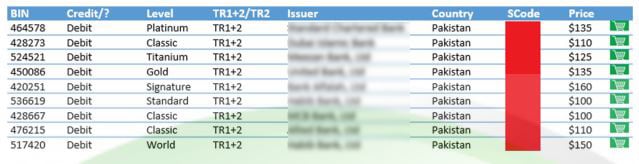
"The data appears to have been acquired through skimming and the hackers have also advertised it as 'skimmed data'," PakCERT CEO Misbahuddin Ahmed told Geo News.
He said the large number of banks affected also showed that the "banks were not digitally compromised", ruling out the likelihood of a traditional cyber attack on the banking system's network servers.
He said the format allows buyers to physically clone the cards for use at Point of sale locations and ATMs.
The SBP's earlier press release, which said compromised cards were cashed out via ATM and POS abroad, also points to the fact that the cards were cloned from 'skimmed data'.
One common way of carrying out this form of card cyber theft is through the card skimming devices.

When a credit or debit card is swiped through a skimmer—often disguised and installed at ATMs and POS—the device captures and stores the details stored in the card's magnetic stripe of chip. Thieves can then use this stolen data to make fraudulent transactions either online or with a cloned counterfeit card.
Misbah said the data was possibly either acquired from compromised ATMs or other places where the hackers had installed skimming devices.
It is unclear exactly where and when these skimmers were installed or where the data in these dumps was acquired from.
As per the background of the hackers, the PakCERT report said there were two possibilities.
"The people who initially did the skimming were visitors from outside Pakistan. They used the cards themselves and then put the dumps for sale on the Darkweb".
Another possibility was that "the people who skimmed were locals and helped a more advaned group outside Pakistan," it added.
"Not much can be done for the data that has already been leaked," said Misbah, but warned others to be on their guard and ensure they check any ATM or any other POS machine before using them.
In a press release on Tuesday evening, Summit Bank said it holds all customer accounts in complete safety and security.
"Summit Bank has been operating normally and securely without facing any cyber threats and there has been no online or card data breach," it said, adding that it was vigilant in monitoring its online services and implementing effective security measures.











